During the early phases of medical device development, an assessment is performed to discover any potential vulnerabilities represented in the proposed device design. These potential vulnerabilities are scored concerning the proposed device’s use cases. In this blog series, Chris Gates, Velentium’s Principal Systems Security Architect, will introduce the core concepts behind vulnerability scoring generally, compare two industry-standard scoring rubrics, CVSS v2 and CVSS v3, for suitability to the medical device design space, and discuss other possible scoring rubrics as well.
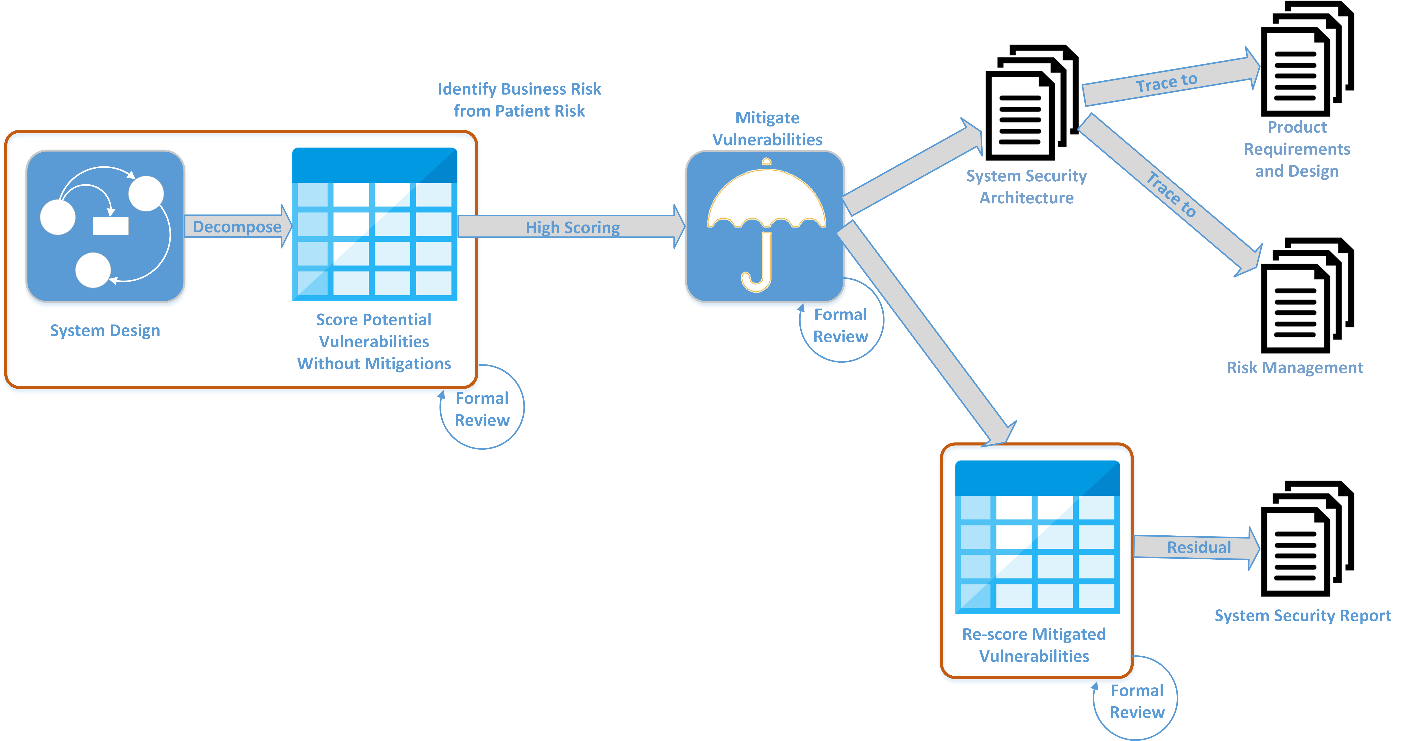
In the early phases of medical device development, a Vulnerability Assessment (VA) must be performed on the proposed medical device. This VA consists of a formal decomposition of the proposed device using an accepted methodology such as STRIDE, Attack Trees, etc., which results in a list of “potential vulnerabilities.” Each of the potential vulnerabilities is evaluated and scored regarding the device's intended use cases.
The initial score assumes that no mitigation exists for the vulnerability. Specifically, the list of scored vulnerabilities is what guides the priority and extent of efficacy for each of the required mitigations.
After the design and selection of mitigations for these scored vulnerabilities, the list of vulnerabilities is re-scored. In this round of scoring, mitigations are included to produce a post-mitigation score for each vulnerability. This second round highlights whether all mitigations are sufficient as designed, or whether additional mitigations are needed for any residual vulnerabilities.
The VA process is included in the overall development cycle, as shown in this diagram:
What is Being Scored?
It is important to emphasize that what is being scored is not “threats,” but rather “vulnerabilities” discovered during the design phase of the device or system. Cybersecurity threats can only be assessed and scored for developed products, while vulnerabilities are assessed against designs.
The VA process we’re describing also does not address vulnerabilities that may be introduced during implementation. It is solely focused on applying a rigorous formal method to expose areas in the design itself that need mitigating security controls.
There are many documented criticisms of existing vulnerability scoring rubrics, and while these criticisms are valid, they are often made in the context of finished, installed devices in the field. For such devices, cybersecurity assessments should be made against “threats,” which are scored and mitigated differently than vulnerabilities. It is critical to apply the right scoring tool to the appropriate point in the product lifecycle: vulnerability assessments are applied during design, implementation vulnerability assessment during development and manufacturing, threat assessments for a product in active use in the field.
Our focus for this series is on vulnerability assessment rubrics used to evaluate the security of a proposed design. When these rubrics are utilized with a design concept instead of a fielded product, they become much more valuable at prioritizing design vulnerabilities, which allows medical device manufacturers to focus on mitigation efforts in specific areas of the design.
In our next post, we’ll kick off our examination of the Common Vulnerability Scoring System (CVSS) from FIRST, a worldwide standard for scoring vulnerabilities across many industries.